Background
Since late 2021 a scammer known as Elliot / Chinese / Devil has stolen $5m+ worth of crypto and NFTs through phishing scams and a NFT rug pull project.
October 2021 — Crazy Lemur Club
On Oct 10 2021 the NFT collection Crazy Lemur Club (CLC) launched with a total supply of 5,000 NFTs created by the anonymous team “Cat” & “Dog”. CLC advertised utility such as “exclusive metaverse access, arcade games, and a community DAO” but on November 5 2021 CLC made its last Tweet ever with the website and Discord being shutdown.

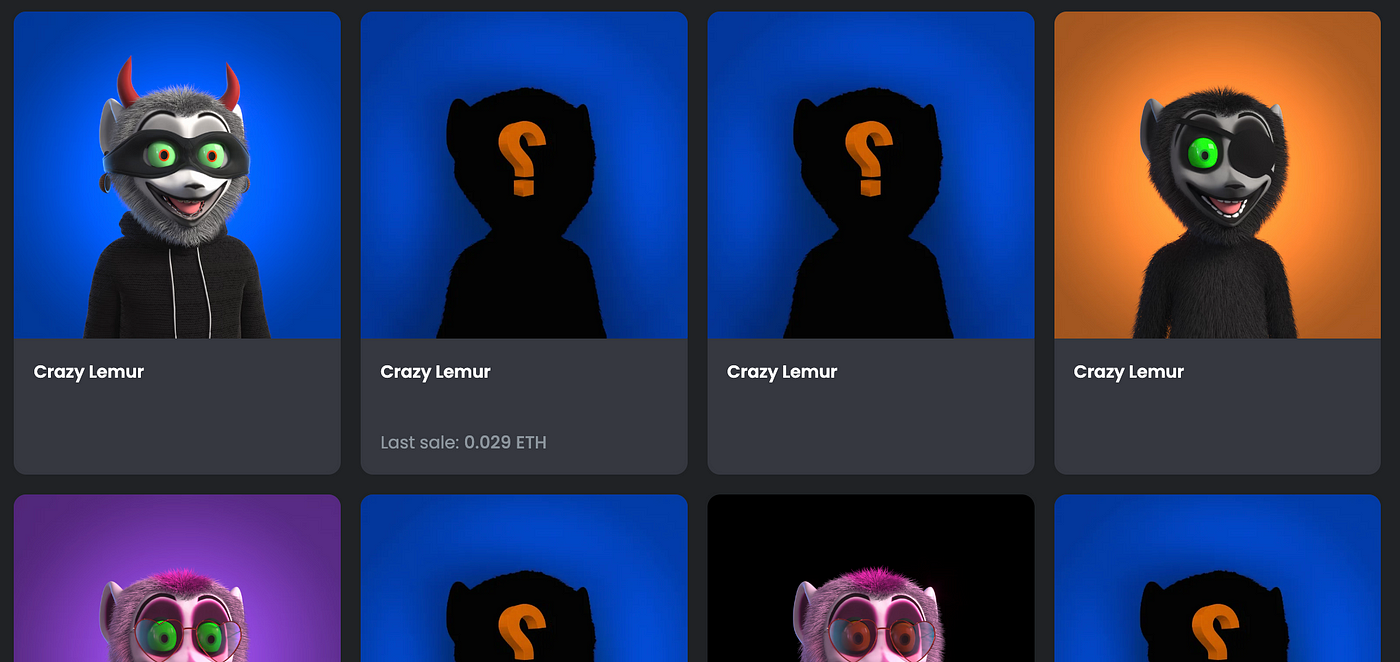
In total CLC had made the team $320k (82 ETH) which was eventually transferred away from the deployers wallets to Tornado Cash. As of Oct 2022 some of the NFTs haven’t even been revealed.
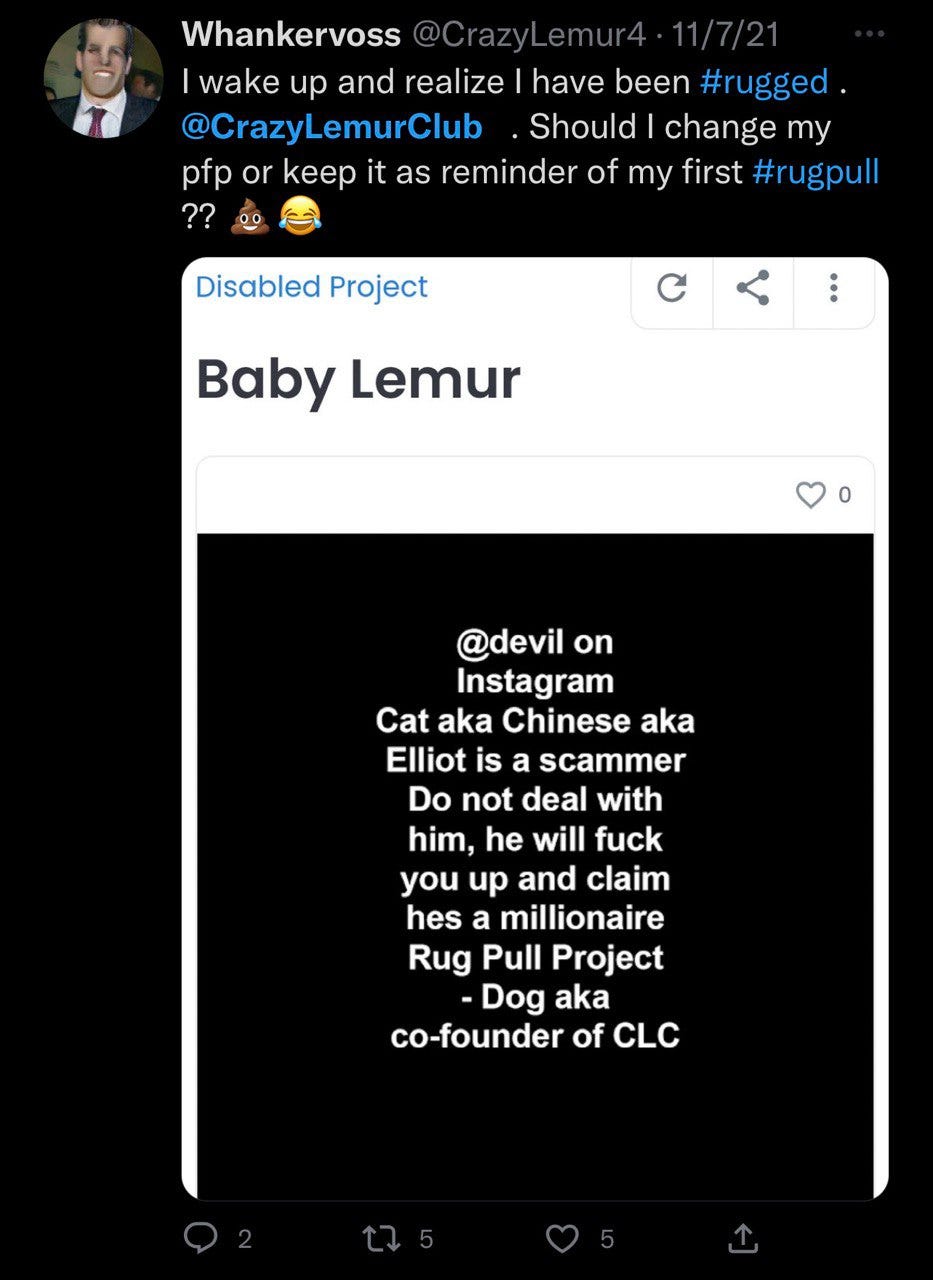
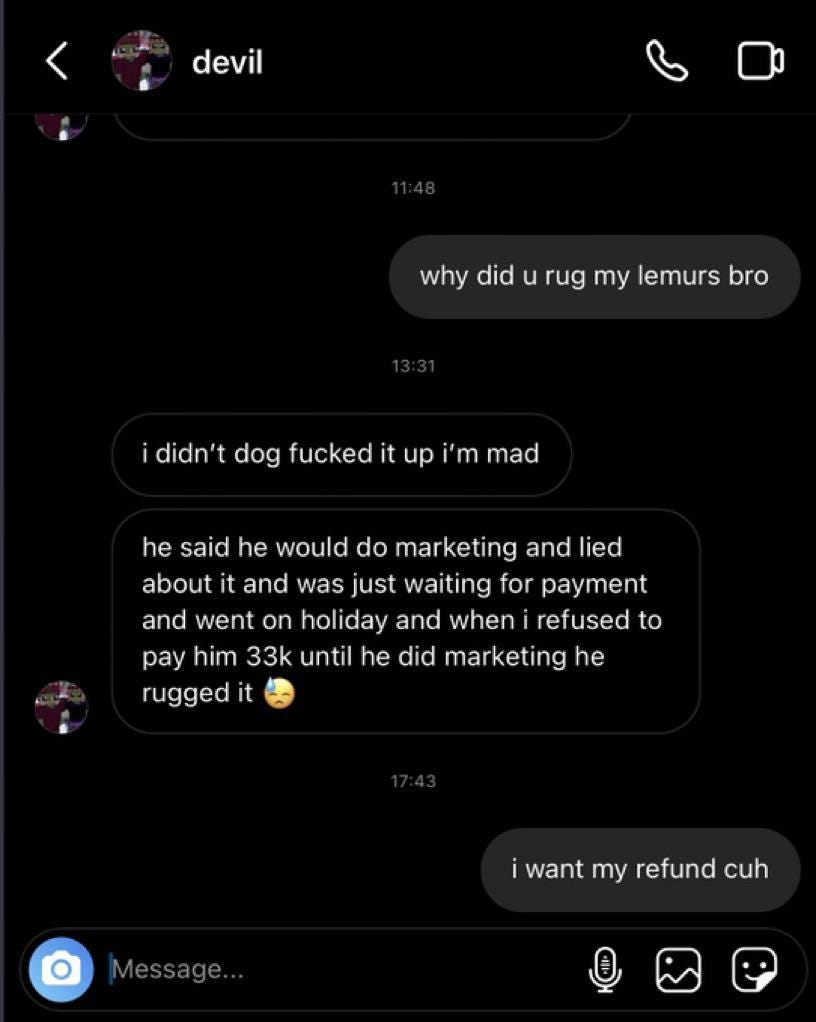
In Nov 2021 the two anon founders got into an argument to where Dog changed the metadata to read “devil on Instagram Cat aka Chinese aka Elliot is a scammer do not deal with him, he will f you up and claim he’s a millionaire”.
One of the victims then proceeded to Tweet about it on Nov 7 2021.
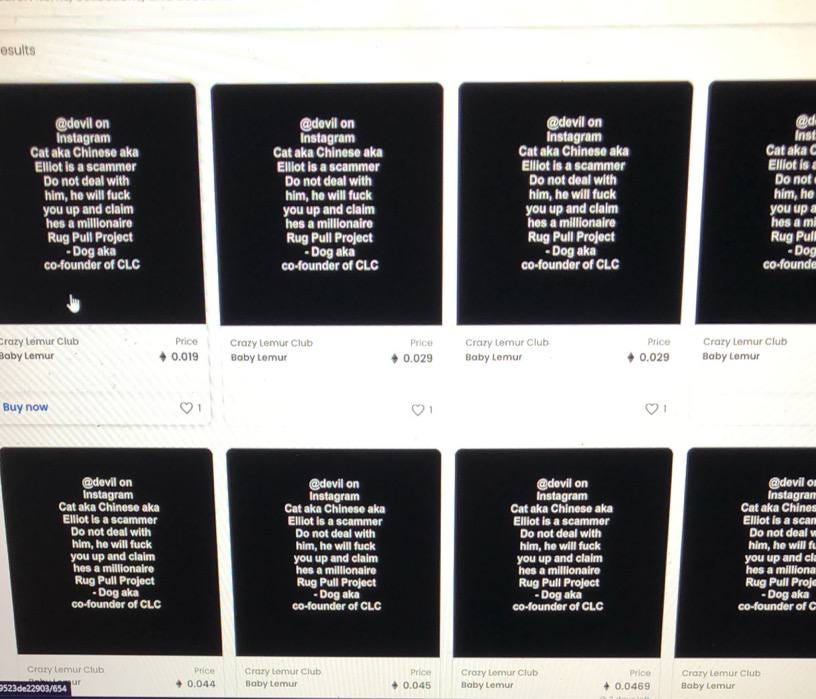
One of the victims confronted Elliott / Devil on Instagram about the rug pull yet he shifted the blame to the other founder Dog and claimed it was simply “marketing” issues.

The funds eventually were all transferred away with no further communication from the team.
January 2022 Part 1
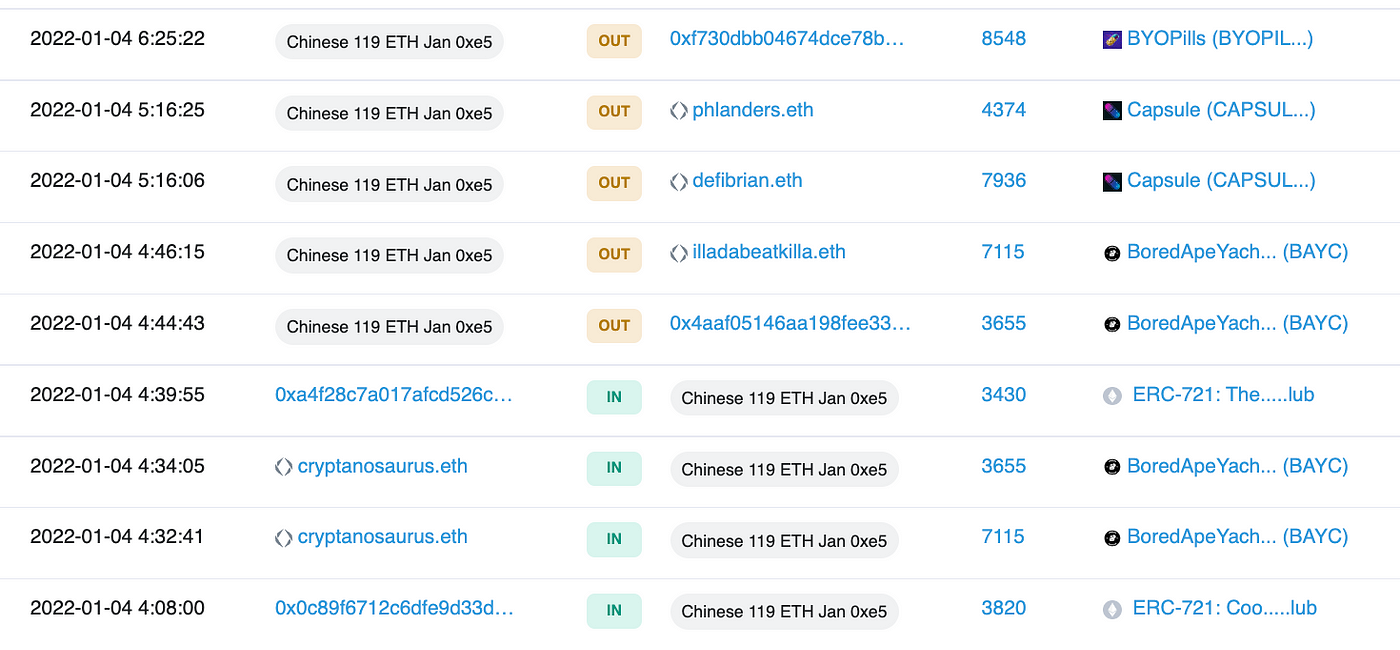
After the CLC rug pull Elliot began to focus on phishing NFTs by creating fake Sudoswap and NFT Trader websites. On January 4 2022 Elliot phished 2 BAYC NFTs from the victim cryptanosaurus.
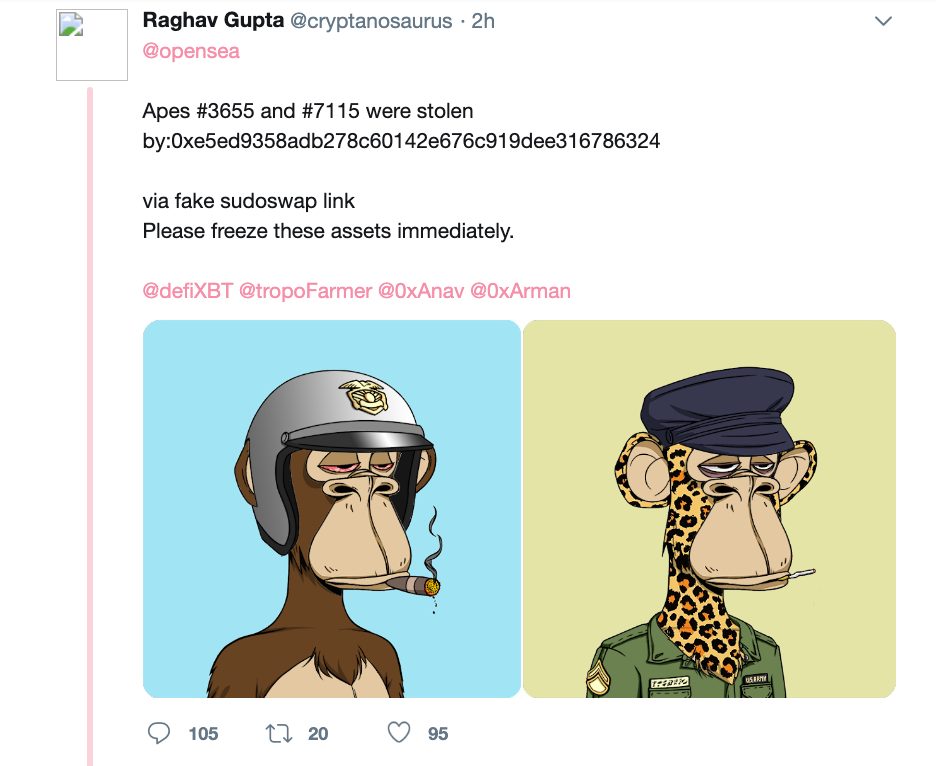
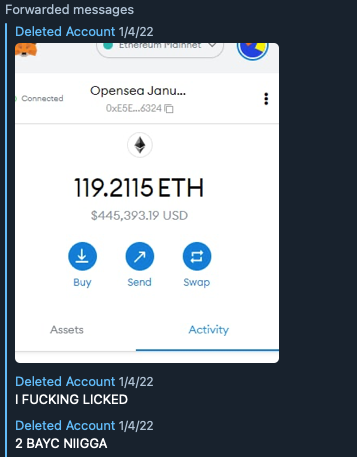
How do we know it was Elliot? From a deleted Telegram account Elliot proceeded to brag about the attack by sharing a screenshot of his Metamask wallet with the stolen funds received.
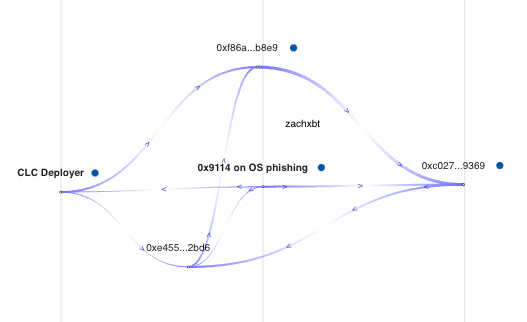
In case you aren’t convinced it was the same scammer here is the phishing attack mapped out in relation to the CLC rug. You can see some of the stolen funds eventually consolidate at 0xc027.
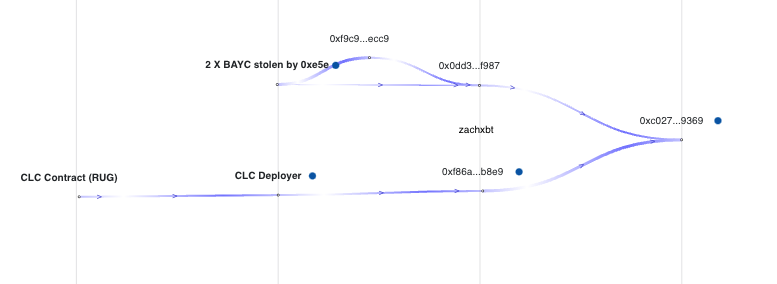
January 2022 Part 2
On January 14 2022 Elliot once again showed off his phishing attacks this time stealing multiple CloneX and various other NFTs using 0x9114, with the username “Matthew Stokey” on OpenSea.
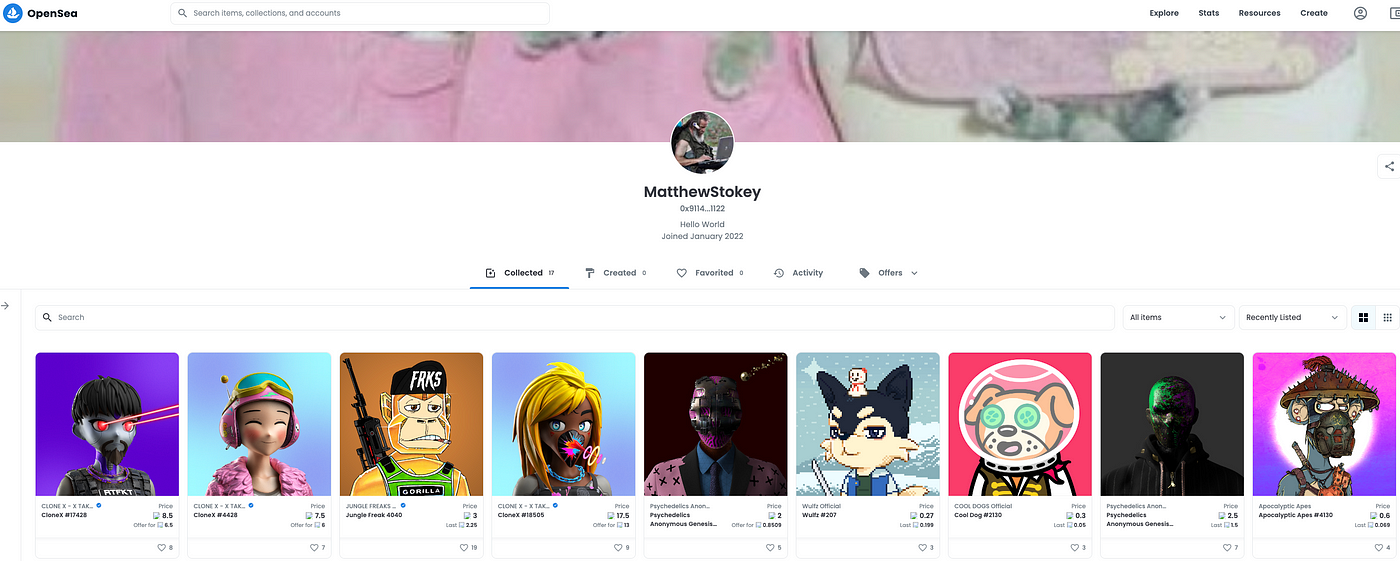
If you search the 0x9114 address on Twitter you will see all of the victims from January 2022 complaining about that address. OpenSea has since banned the address .

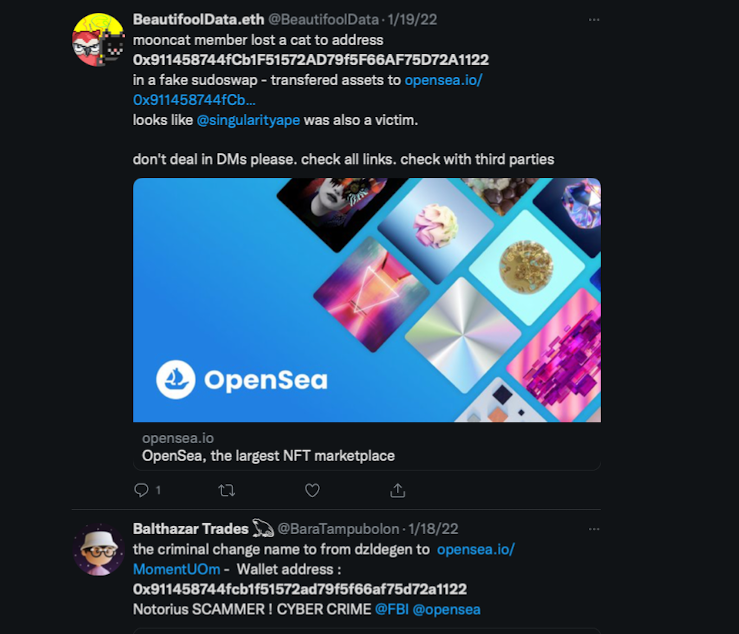
If you map out the 0x9114 address you will see how it is directly tied to the CLC deployer before then consolidating at the 0xc027 address.
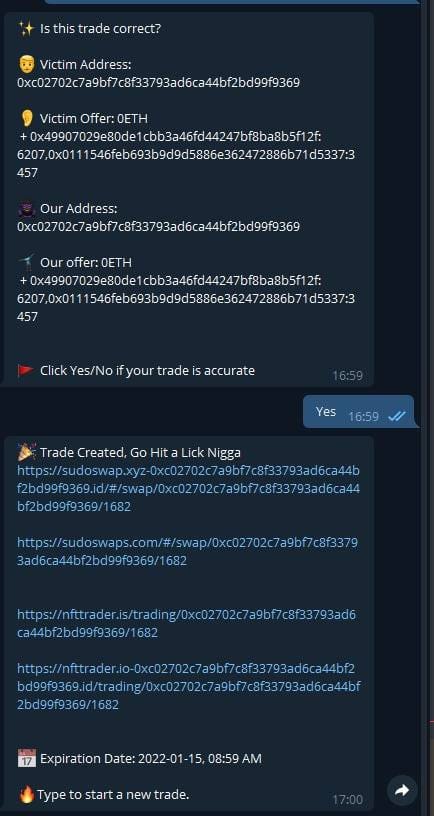
Here is another screenshot of what Elliot would see on Telegram when creating “trades” on the fake Sudoswap and NFT Trader sites.
Once again the address is 0xc02702c7A9BF7c8F33793aD6Ca44Bf2bd99f9369
February 2022
On Feb 1 Twitter user bo66ydigital was phished for 1 BAYC and 2 MAYC NFTs. Again the address used to scam was tied to both 0x9114 and 0xc027.

Tornado Deposits
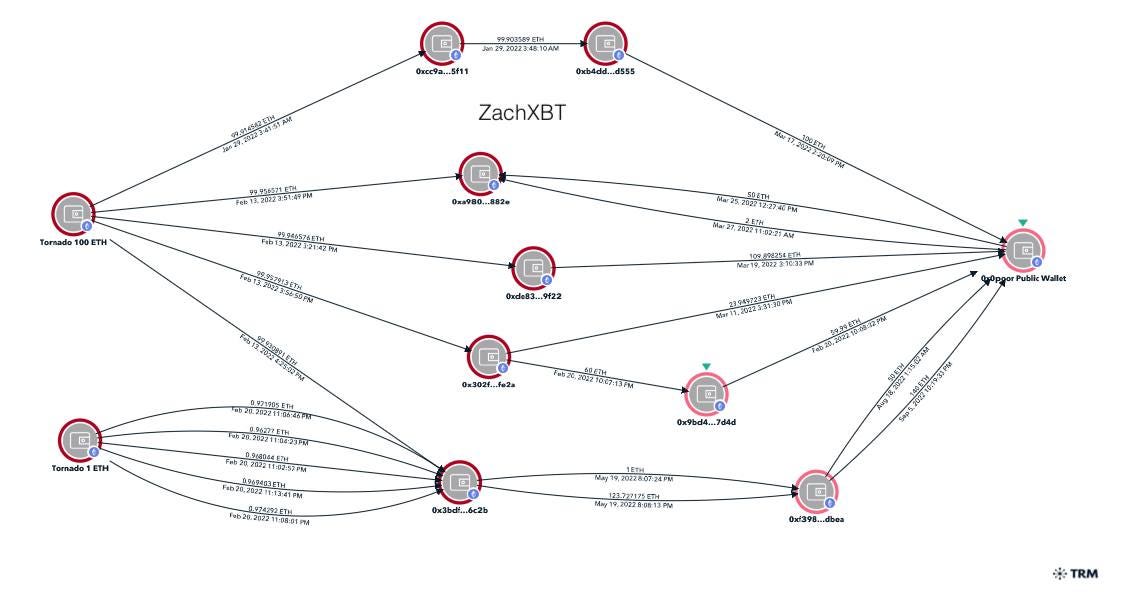
With the stolen funds Elliot made many Tornado deposits in early 2022 from the various phishing scams. From the 0xc027 address 100 ETH was deposited into Tornado on January 29.
Shortly after on February 13, 400 ETH was moved from 0xc027 to 0x328f before being deposited into Tornado over the next few days. From 0x328f in total $1.25m (445 ETH) was sent to Tornado.

Other phishing scams are linked to Elliot from 0x328, 0xb2a8, 0x215, 0xb52, 0xa0e, 0x5c8, 0x0141 which have collectively deposited over $3.3m (1165 ETH) into Tornado from Jan 2022 — Apr 2022. Another 434 ETH sits in wallets that’ve been dormant for months.
0x0Poor aka Elliot
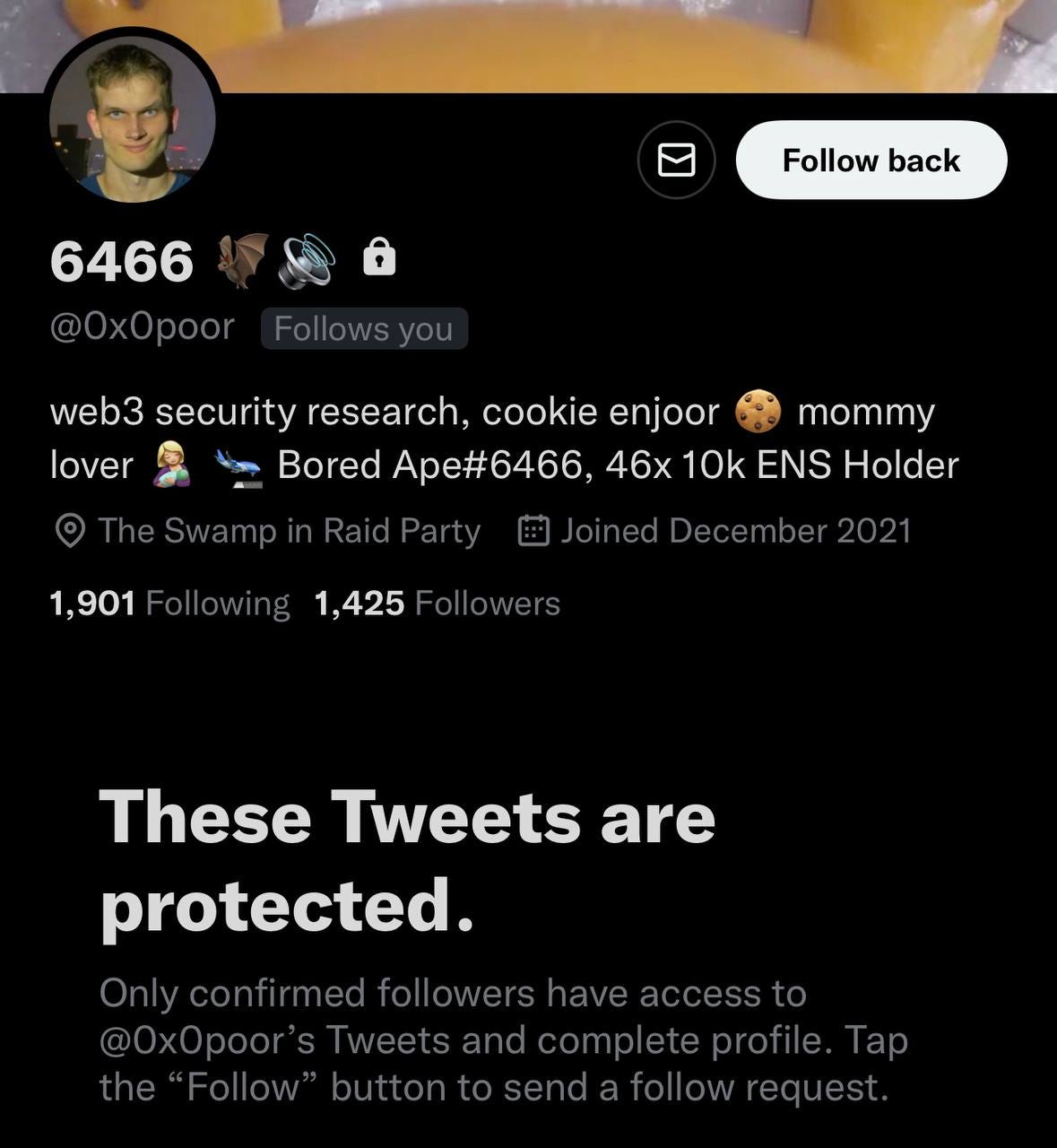
In February 2022 a mysterious new BAYC owner popped up on Twitter, Discord, and OpenSea who went by “0x0poor” using an address which had been almost entirely funded via Tornado Cash.
Interestingly just like for the Tornado deposits 0x0poor received 1 X 100 ETH withdrawal on January 29 and subsequently 4 x 100 ETH and 5 x 1 ETH in February from Tornado later matching the deposits shared above 1:1.
While he did not withdraw the exact amount to one single address immediately after depositing, Elliot instead later consolidated the Tornado withdrawals into his public address a few hops out in the weeks following a withdrawal.
The stolen funds were then used to buy a variety of NFTs. Elliot currently holds BAYC 6466 and 46 x 10k ENS domains in his portfolio.
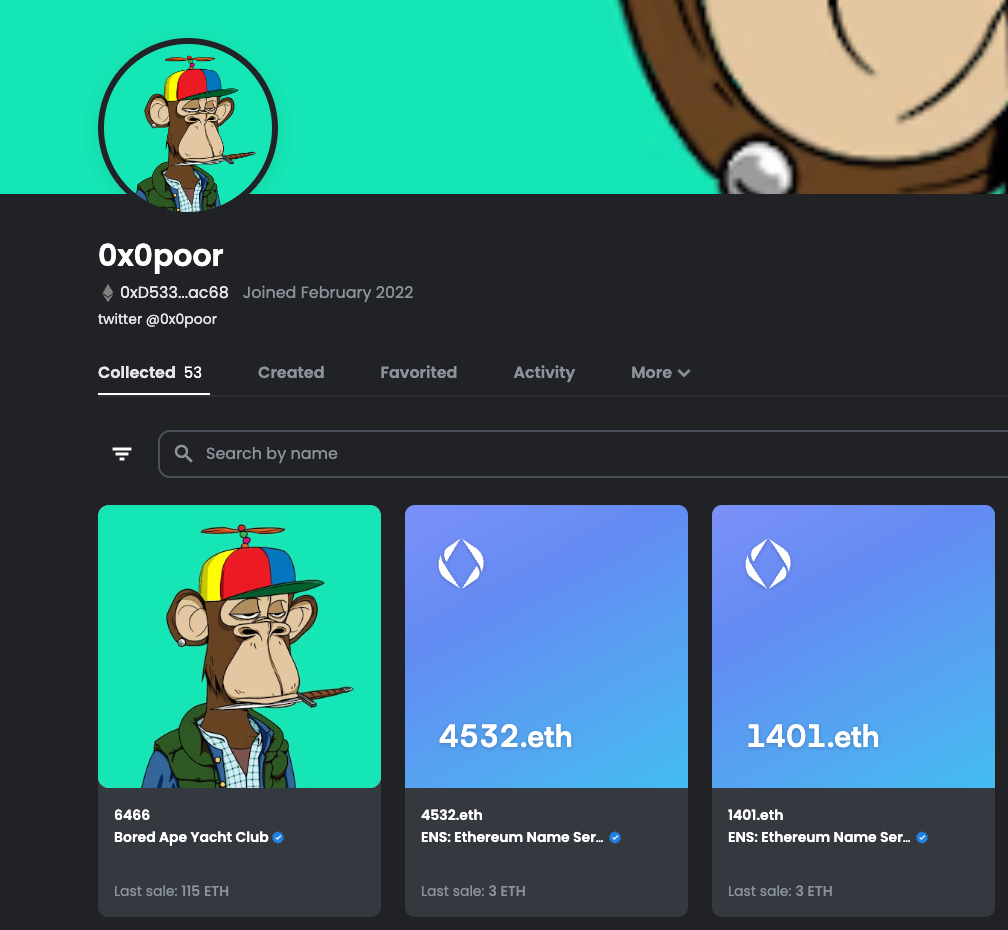
0x0poor placed a 5 WETH offer on the ENS domain ‘elliot.eth’ in July 2022 further solidifying he is the same phishing scammer.

Using his BAYC profile picture I was able to match it to the Instagram user ‘$ex’.


Elliot would also share posts with the Instagram user ‘Nikola’ who appears to be his girlfriend. Notice how the roofing is the exact same as in Elliot’s Instagram story.
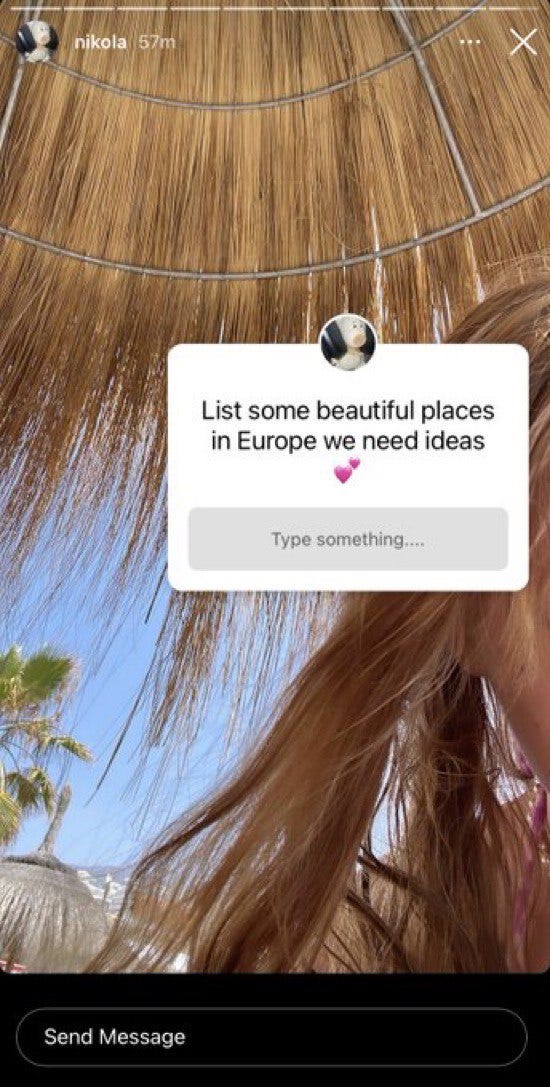
Elliot is quite active in the Bored Ape Yacht Club Discord with 55+ pages of messages (Discord ID: 920842415412224021). On May 29 Elliot posted that he was in Tenerlife at a villa.

His gf then posted a video at the same villa on Tiktok the next day.
She also would post tons of other videos with Elliot in the background and of her splurging on designer clothing or luxury travel presumably using the stolen funds.
In recent months Elliot appears to be a customer of the scammer ‘Monkey Drainer’. Last week I messaged MD on Telegram where a customer of MD accidentally then messed up. I temporarily added his username to my Twitter bio which was then flexed in the MD announcement channel minutes after.

Using the “Followed by Wayvern, jETHski.eth and 761 others you follow” I was also able to narrow the account down to Elliot. How might you ask? Well it turns out the Twitter user ‘itsWayvern’ only has 87 total followers with one of them being 0x0poor aka Elliot.



Once I had this I then checked to see if 0x0poor followed 0xjetski, which in fact he did. I then exported his following list to confirm the total number followed also matched the screenshot as well.


To check for any on-chain ties I started with the 0x0poor public wallet and mapped out the transactions to find that the wallet is only 2–3 hops away from Monkey drainer ENS and federalagent👮♂.eth . The 0xc027 Tornado deposit wallet from earlier in this article is also only a few hops away from Monkey Drainer’s main wallets proving Elliot is a customer.

It’s disgusting to see a phishing scammer steal millions in the span of a few months and then use it to buy designer clothing, NFTs, and travel around the world living lavishly. Hopefully now that it is known Elliot is behind many recent phishing scams the victims will be able to take some sort of legal action to potentially recover funds in the future.
A huge thanks goes out to Bisamazen who created the amazing cover photo for this article and also bax1337 who helped review some of the transactions I found.
Donations
If you find research such as this particularly interesting or perhaps if you were a victim of Elliot yourself please consider donating to my address. My work is entirely community funded with hundreds of hours going into articles such as this.
0x9D727911B54C455B0071A7B682FcF4Bc444B5596
zachxbt.eth
BTC:
bc1qw56fn670purjq5wvyr7w875q3h75hgkawnruy4lkxmx0ruapdj2ss03kw7
Gitcoin: